ModSecurity WAF Guide
This comprehensive guide covers ModSecurity Web Application Firewall (WAF) configuration in the Nginx WAF Management Platform, including OWASP Core Rule Set (CRS) management, custom rule creation, and advanced security configurations.
Overview
ModSecurity is a web application firewall that protects your web applications from various attacks, including:
- SQL Injection (SQLi): Prevents database injection attacks
- Cross-Site Scripting (XSS): Blocks malicious script injection
- Remote File Inclusion (RFI): Prevents inclusion of remote files
- Local File Inclusion (LFI): Blocks local file access attempts
- Command Injection: Prevents system command execution
- Session Fixation: Protects against session hijacking
- Authentication Bypass: Blocks unauthorized access attempts
ModSecurity Interface
Access ModSecurity settings by:
- Click Domains in the sidebar
- Select a domain from the list
- Click the ModSecurity tab
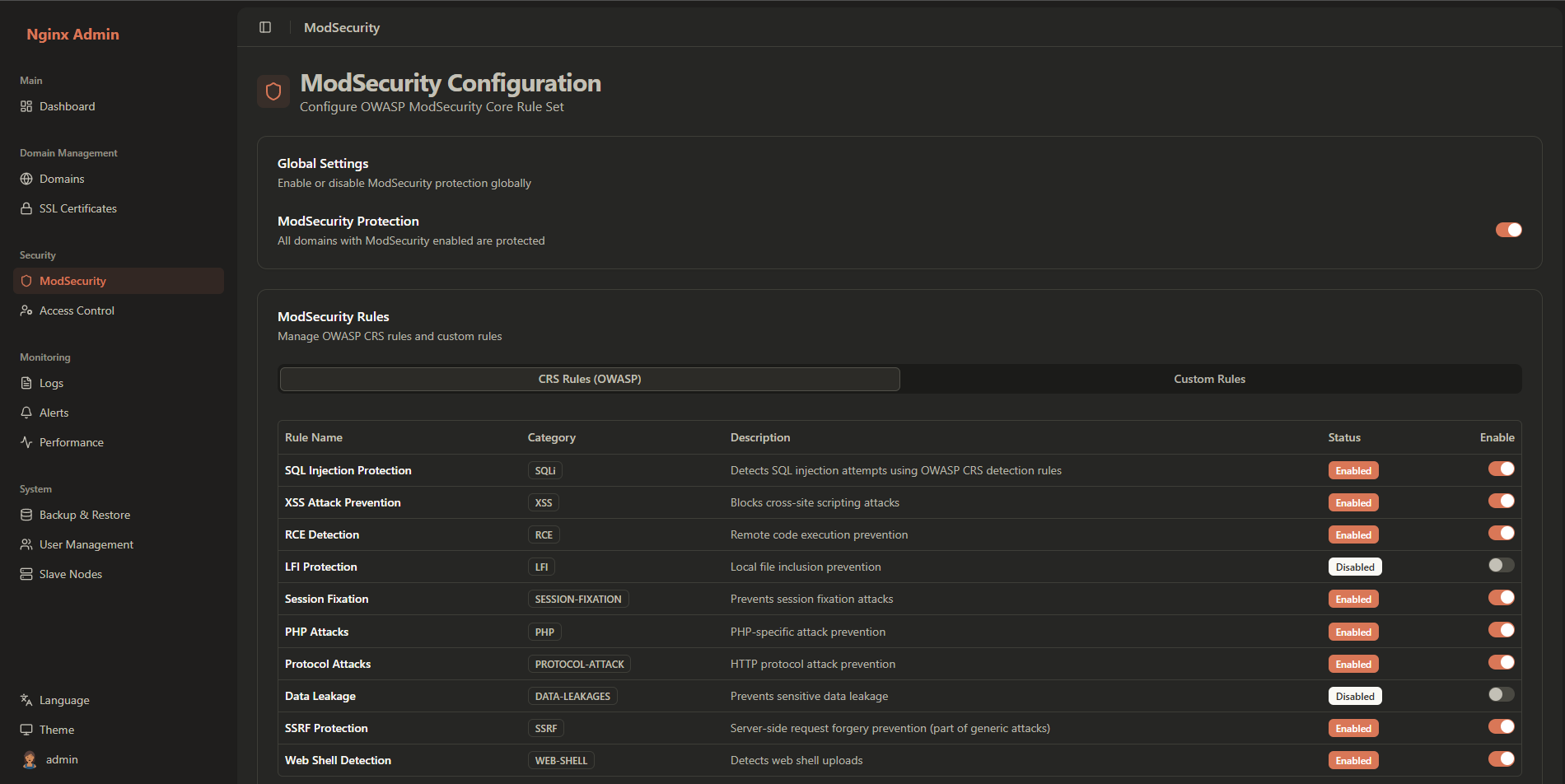
The ModSecurity interface provides:
- Global Settings: Enable/disable ModSecurity globally
- CRS Rules: OWASP Core Rule Set management
- Custom Rules: User-defined security rules
- Rule Categories: Organized rule categories
- Paranoia Levels: Security sensitivity settings
Enabling ModSecurity
Global ModSecurity Settings
- Click ModSecurity in the sidebar
- Configure global settings:
- Enable ModSecurity: Turn on WAF protection
- Default Paranoia Level: Set default security level
- Audit Logging: Enable/disable security event logging
Domain-Specific ModSecurity
- Select a domain from the list
- Click the ModSecurity tab
- Toggle Enable ModSecurity for this domain
- Configure domain-specific settings
OWASP Core Rule Set (CRS)
The OWASP CRS is a set of generic attack detection rules that provide protection against many common attack categories.
CRS Rule Categories
1. Request Rule Set
- REQUEST-930-APPLICATION-ATTACK-LFI: Local file inclusion attacks
- REQUEST-931-APPLICATION-ATTACK-RFI: Remote file inclusion attacks
- REQUEST-932-APPLICATION-ATTACK-RCE: Remote code execution attacks
- REQUEST-933-APPLICATION-ATTACK-PHP: PHP injection attacks
- REQUEST-941-APPLICATION-ATTACK-XSS: Cross-site scripting attacks
- REQUEST-942-APPLICATION-ATTACK-SQLI: SQL injection attacks
- REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION: Session fixation attacks
Managing CRS Rules
Enable/Disable Rule Categories
- Select your domain
- Click the ModSecurity tab
- View available rule categories
- Toggle categories on/off as needed
Configure Individual Rules
- Click on a rule category to expand it
- View individual rules within the category
- Toggle specific rules on/off
- Configure rule-specific settings
Custom Rules
Create custom ModSecurity rules for application-specific security requirements.
Rule Syntax
ModSecurity rules follow this syntax:
SecRule VARIABLES OPERATOR [ACTIONS]Example Custom Rules
Block SQL Injection Attempts
SecRule ARGS "@detectSQLi" \
"id:1001,\
phase:2,\
block,\
msg:'SQL Injection Attack Detected',\
logdata:'Matched Data: %{MATCHED_VAR} found within %{MATCHED_VAR_NAME}',\
tag:'application-multi',\
tag:'language-multi',\
tag:'platform-multi',\
tag:'attack-sqli'"2
3
4
5
6
7
8
9
10
Block XSS Attempts
SecRule ARGS "@detectXSS" \
"id:1002,\
phase:2,\
block,\
msg:'XSS Attack Detected',\
logdata:'Matched Data: %{MATCHED_VAR} found within %{MATCHED_VAR_NAME}',\
tag:'application-multi',\
tag:'language-multi',\
tag:'platform-multi',\
tag:'attack-xss'"2
3
4
5
6
7
8
9
10
Block Bad User Agents
SecRule REQUEST_HEADERS:User-Agent "@pmFromFile bad-user-agents.data" \
"id:1003,\
phase:1,\
block,\
msg:'Bad User Agent Blocked',\
logdata:'Matched Data: %{MATCHED_VAR} found within %{MATCHED_VAR_NAME}',\
tag:'application-multi',\
tag:'language-multi',\
tag:'platform-multi',\
tag:'attack-useragent'"2
3
4
5
6
7
8
9
10
Rate Limiting
SecRule IP:@ipMatch "192.168.1.0/24" \
"id:1004,\
phase:1,\
nolog,\
pass,\
ctl:ruleEngine=Off"2
3
4
5
6
Creating Custom Rules
Select your domain
Click the ModSecurity tab
Click Add Custom Rule
Fill in rule details:
- Name: Descriptive rule name
- Category: Rule category (e.g., "Custom Security")
- Rule Content: ModSecurity rule syntax
- Description: What the rule does
- Enabled: Enable/disable the rule
Click Save
Rule Variables
ModSecurity provides various variables for rule matching:
Request Variables
ARGS: All request parametersARGS_NAMES: Parameter namesARGS_GET: GET parametersARGS_POST: POST parametersREQUEST_HEADERS: Request headersREQUEST_COOKIES: Request cookiesREQUEST_URI: Request URIREQUEST_METHOD: HTTP methodREQUEST_BODY: Request body
Response Variables
RESPONSE_HEADERS: Response headersRESPONSE_BODY: Response bodyRESPONSE_STATUS: HTTP status code
Operators
ModSecurity provides various operators for pattern matching:
String Operators
@rx: Regular expression match@pm: Phrase match (any of the phrases)@pmFromFile: Phrase match from file@contains: Contains string@beginsWith: Begins with string@endsWith: Ends with string
Numeric Operators
@eq: Equal to@gt: Greater than@lt: Less than@ge: Greater than or equal to@le: Less than or equal to
Special Operators
@detectSQLi: SQL injection detection@detectXSS: XSS detection@validateUtf8Encoding: UTF-8 validation@validateByteRange: Byte range validation
Rule Actions
ModSecurity supports various actions for rule processing:
Disruptive Actions
- deny: Deny the request with a 403 status
- block: Block the request (depends on configuration)
- drop: Drop the connection
- redirect: Redirect to another URL
- pass: Continue processing (no action)
Flow Actions
- phase: Set processing phase (1-5)
- t:none: No transformation
- **t:lowercase`: Convert to lowercase
- **t:urlDecode`: URL decode
- **t:htmlEntityDecode`: HTML entity decode
Data Actions
- log: Log the rule match
- nolog: Do not log the rule match
- auditlog: Write to audit log
- noauditlog: Do not write to audit log
Metadata Actions
- id: Unique rule identifier
- msg: Rule message
- logdata: Additional log data
- tag: Rule tags
- severity: Rule severity (1-5)
Advanced Configuration
Exception Handling
Create exceptions for legitimate traffic that might be blocked:
IP Whitelist
SecRule REMOTE_ADDR "@ipMatch 192.168.1.100" \
"id:2001,\
phase:1,\
nolog,\
pass,\
ctl:ruleEngine=Off"2
3
4
5
6
URI Whitelist
SecRule REQUEST_URI "@beginsWith /api/public/" \
"id:2002,\
phase:1,\
nolog,\
pass,\
ctl:ruleRemoveById 941100"2
3
4
5
6
Parameter Whitelist
SecRule ARGS:product_code "@rx ^[A-Z0-9-]+$" \
"id:2003,\
phase:2,\
nolog,\
pass,\
ctl:ruleRemoveTargetById 942100;ARGS:product_code"2
3
4
5
6
Anomaly Scoring
Configure anomaly scoring for advanced threat detection:
# Set anomaly score threshold
SecAction "id:9001,\
phase:1,\
nolog,\
pass,\
t:none,\
setvar:tx.anomaly_score_threshold=5"
# Increase anomaly score for suspicious requests
SecRule ARGS "@detectSQLi" \
"id:9002,\
phase:2,\
pass,\
msg:'SQL Injection Attempt',\
logdata:'Matched Data: %{MATCHED_VAR} found within %{MATCHED_VAR_NAME}',\
tag:'attack-sqli',\
setvar:tx.anomaly_score=+3"
# Block high anomaly scores
SecRule TX:ANOMALY_SCORE "@gt %{tx.anomaly_score_threshold}" \
"id:9003,\
phase:2,\
block,\
msg:'Anomaly Score Exceeded'"2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
For more information on related topics: